An Innovative Approach to Uncover — and Fix — Hidden Cyber Risk from Rocketgraph+Threatworx: ASM++
The Flaw In Our Thinking about ASM
In cybersecurity, the real threat isn’t the vulnerabilities you see, it’s the hidden connections that you don’t. Attackers look beyond isolated vulnerabilities, chaining together unseen pathways to reach your most valuable assets. Most security tools still treat vulnerabilities as standalone issues, but attackers seek out connected routes. I would assert that perhaps our entire mental model for cyber risk is flawed.
The October 2025 F5 breach proved the point. A nation-state actor used a known vulnerability to steal source code and erased $1.3 billion in shareholder value. Both the flaw and the malware were public knowledge. The real question: why didn’t they see the path to disaster?
I had the opportunity to attend a Rocketgraph and Threatworx’s webinar entitled “ASM++: How To Find (and Fix) Hidden High Value Vulnerabilities.” It introduced a new approach: stop managing risk as a checklist, start understanding it as a graph. The difference isn’t academic. It is the key to seeing the attack paths your tools miss.
Forrester defines attack surface management (ASM) as “… the process of continuously discovering, identifying, inventorying, and assessing the exposure of an entity’s IT asset estate.”
The ++ in ASM++ is the Rocketgraph+Threatworx’s dramatic take on the ASM definition implying an enhanced, more comprehensive, “next-generation” form of standard ASM that emphasizes advanced capabilities such as the use of AI, business context, and graph technology to extend the ASM definition to include discovery and remediation of the said IT asset estate.
The webinar was emceed by Walt Maguire, VP of Product for Rocketgraph, and featured David Haglin, Ph.D., Co-founder and CTO of Rocketgraph, and Ketan Nilangekar, Co-founder and CEO of Threatworx.
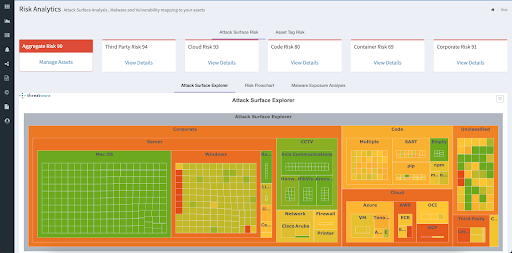
The following are my 5 key takeaways from the webinar.
1. The True Blast Radius Of A Single Breach Can Be Terrifyingly Large
The ‘blast radius’ is the total damage an attacker can inflict after breaking in. Breaches don’t stop at the entry point. They spread in hops, from L0 to L1, L2, and beyond, touching every connected system.
The centerpiece of the session was a live demo that illustrated this and several related concepts.
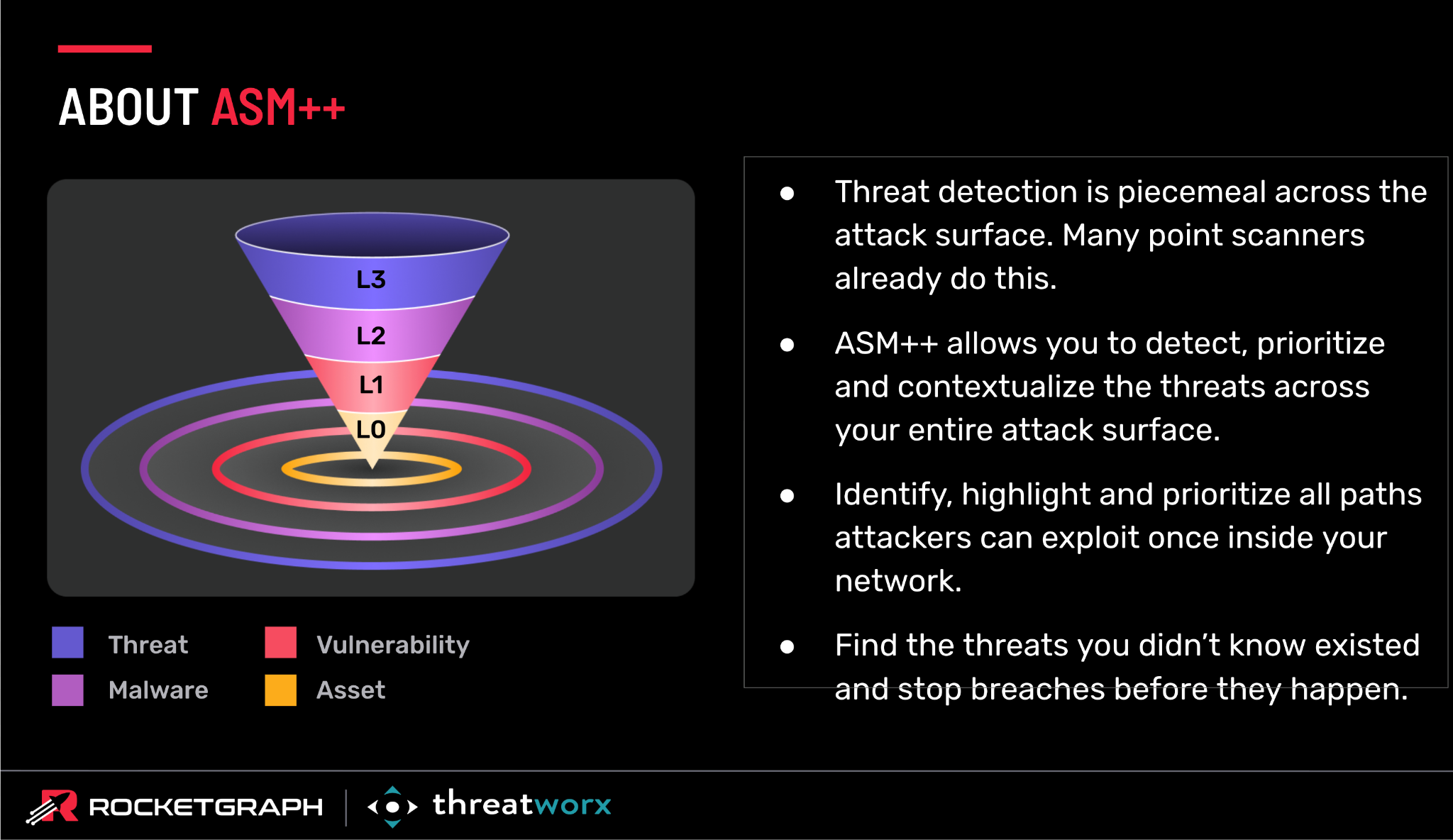
The scenario started from just two compromised VPN servers. At the first hop (L1), the impact looked contained, impacting 2 of 181 assets. At the second hop (L2), it had spread to 82 assets, or 45% of the total. But by the third hop (L3), the blast radius had exploded to encompass 173 out of 181 assets. That is over 95% of the company’s entire infrastructure.
Let’s net that out. A single breach of a single VPN server and exploits of two known vulnerabilities could give bad actors access to virtually the entire business.
Hardening the perimeter alone isn’t a strategy. The real damage happens in the unseen hops where risk multiplies. Treating vulnerabilities as isolated points is a relic of the past.
The Takeaway: If you don’t think in terms of attack paths, you’re implicitly assuming attackers stop after initial access. On the contrary, they are just getting started.
2. Security Tools See Dots. Attackers See Lines.
Most detection tools are still operating with blinders on, scanning for isolated issues while missing the bigger picture. That is exactly the gap attackers exploit. They aren’t looking for a high vulnerability count; they are looking for the path of least resistance to your assets.
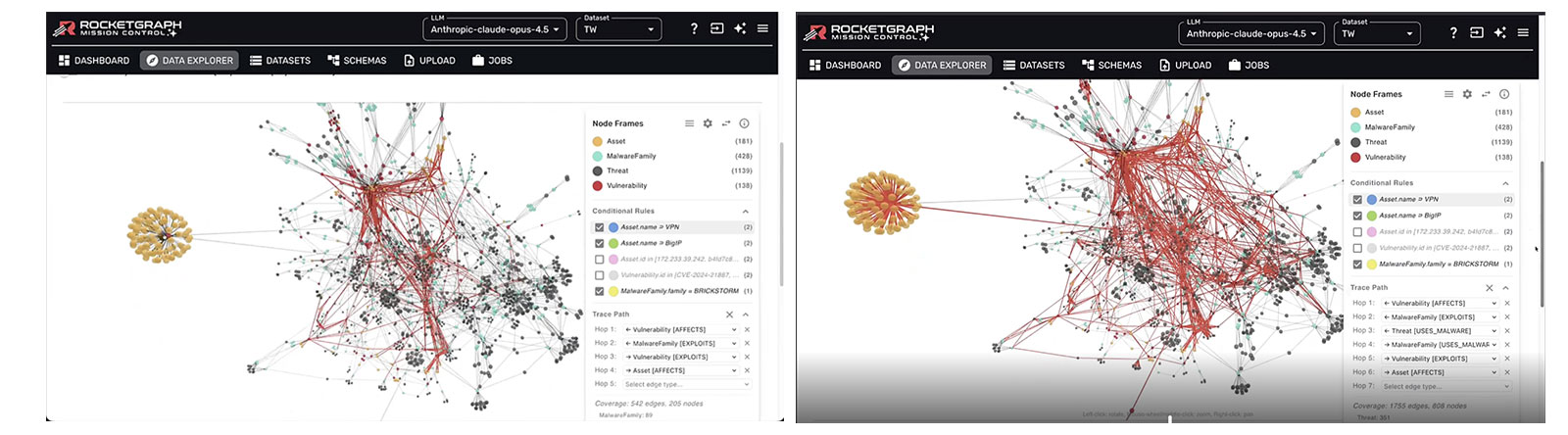
The “dandelion” visual in the demo drove home this point. You have a cluster of high-value assets (such as source code) that appears safe in a standard scan. But when you apply graph analysis, you suddenly see a hidden three-hop path, connecting that “safe” cluster straight to a compromised VPN.
This new insight changes the strategy entirely, from trying to patch everything to finding “choke points”. Sever those, and the entire attack path collapses.
The Takeaway: Your high-value assets may look safe, but attackers will find the indirect routes your current tools can’t see.
3. Context Beats Severity Every Time
Relying solely on the National Vulnerability Database (NVD) may leave you, well, vulnerable! We saw a perfect example of this: a critical vulnerability had been known for months, yet the NVD still hadn’t updated the CVSS score. That lag isn’t just a delay; it’s an open invitation for attackers.
You cannot wait for an official score to tell you something is dangerous. You need to know if it’s dangerous to you now. Real-time context will always outperform a static score.
As Ketan commented, “They’re a government organization … doing this analysis for each and every CVE that pops up. It’s slow… they’re always in catch-up mode.”
To solve this, Threatworx’s AI-driven curation engine continuously scours not just official databases but also vendor advisories, security bulletins, and GitHub repositories. This intelligence feed is piped into the graph daily. By applying real-world exploitability and environmental context, ASM++ can auto-close up to 90% of “High” severity tickets that pose no practical risk, freeing teams to focus on threats with a viable path to impact.
The Takeaway: Severity is a property of a CVE. Risk is a property of your environment.
4. AI Needs To Drive Remediation, Not Just Discovery
Finding vulnerabilities has never been the bottleneck. It is fixing the critical ones before an attacker does.
We need to stop viewing AI as just a scanner. It should serve as scaffolding for your engineers, generating patch scripts, remediation steps, and deployment-ready code fixes.
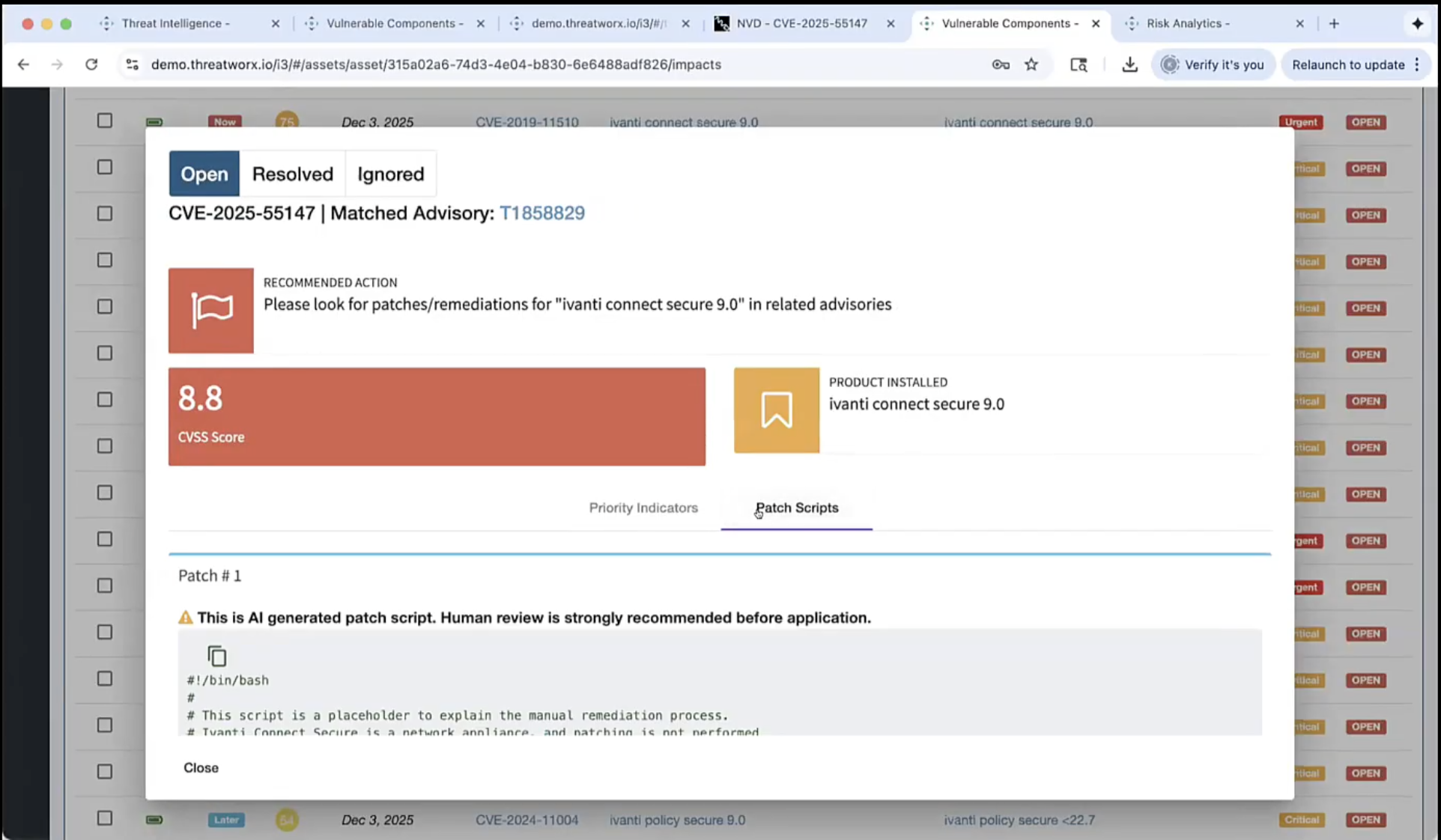
This is about agility. You eliminate the handoffs and the “translation layers” between security findings and engineering action. Zero lag. Instant remediation.
The Takeaway: Detection is cheap. Operationalizing the fix is what reduces breach probability.
5. You No Longer Need to Be a Graph Expert to Find Hidden Threats
Graph analysis, which is superpowerful, has historically been inaccessible to most security leaders because it requires specialized knowledge of query languages such as Cypher.
The demo showed how Rocketgraph’s “AI-first user experience” eliminates this barrier. Using Claude Opus 4.5, the platform allows a user to ask complex, strategic questions in plain English, such as, “Find vulnerabilities that affect multiple high-value assets but aren’t widely exploited yet.” The AI translates this into the necessary query to search the graph.
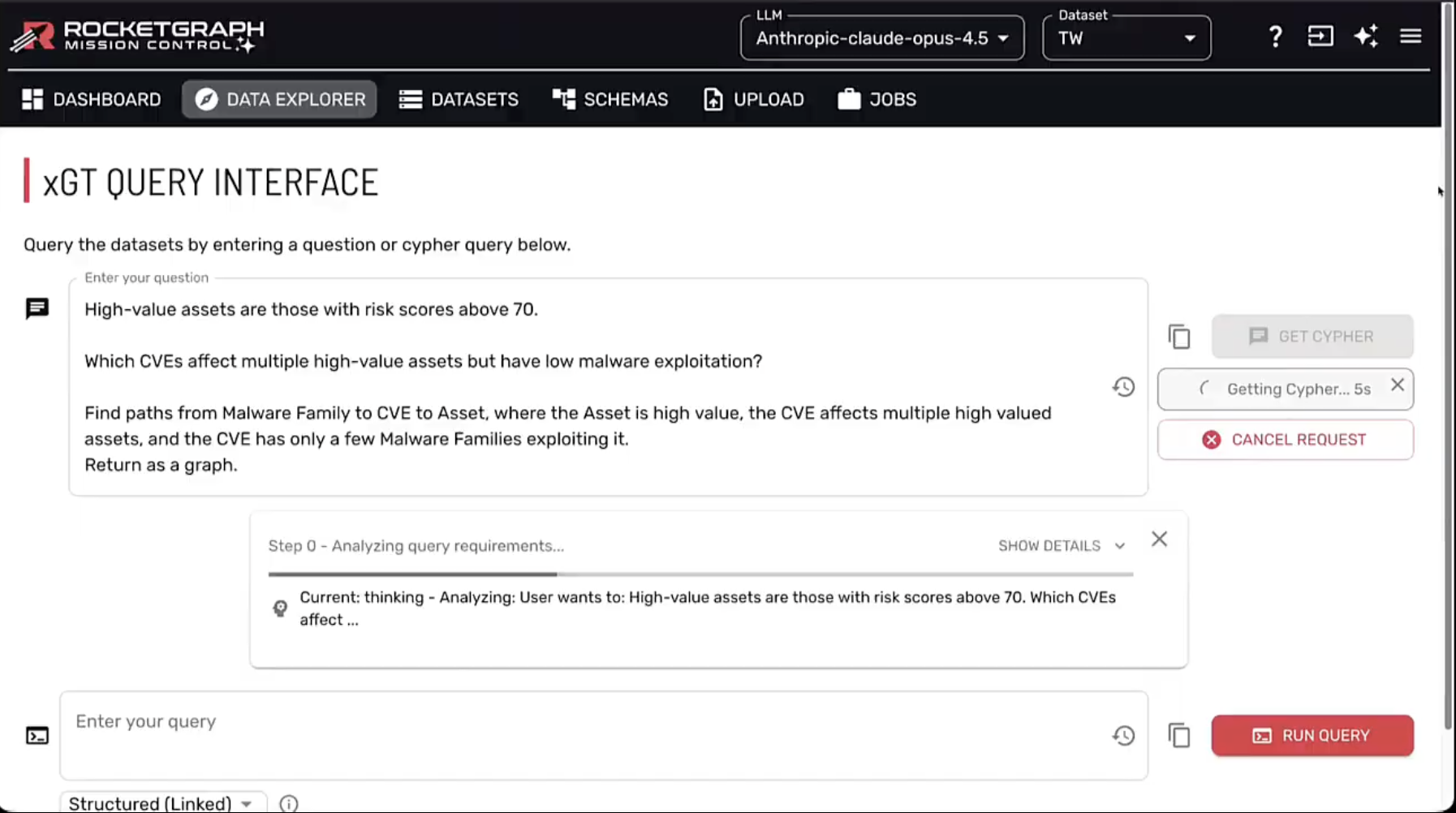
To quote David, “CISOs are not going to want to learn how to write Cypher queries. But they want to know how to ask questions about their graph.”
The Takeaway: AI is making advanced threat hunting accessible to those who need it.
Conclusion
The core message: cybersecurity isn’t about listing vulnerabilities anymore. The future is mapping the web of relationships between assets, vulnerabilities, and threats, zeroing in on what matters, and fixing it. Why did the F5 breach happen? They only saw the dots, not the invisible lines that led attackers straight to their crown jewels.
You know the vulnerabilities in your environment. But do you know the paths they open to your crown jewels?
Want to Learn More?
You may replay the webinar using this link. For more information, contact Walt Maguire at Rocketgraph by emailing wa**@*********ph.com.




